



















Project Overview
Main Idea
With the increasing convergence of communication to IP-based
networks, dynamic and adaptive protection against security threats
becomes a critical requirement. Unfortunately, convergent
communication is characterized by complex network protocols,
heterogeneous infrastructures and a multitude of user
devices. Today's security instruments fail to cope with this
diversity; communication services as well as clients regularly
fall victim to network attacks and malicious software.
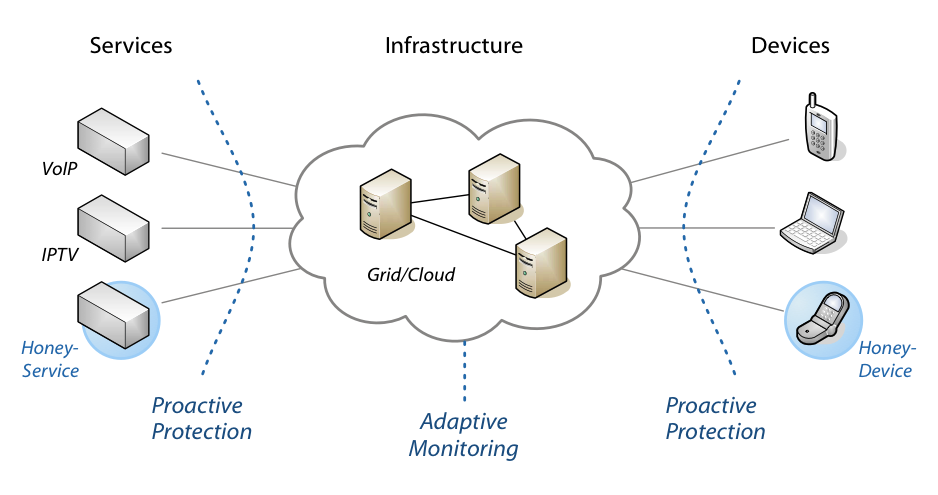
The project PROSEC aims at establishing a holistic protection
for convergent communication. This protection builds on three
layers: (a) the protection of services, (b) the protection of
devices, and (c) the adaptive monitoring of the infrastructure. The
following figure shows these three layers. Information about
current threats are collected using dynamic decoys and analysed
with machine learning for automatically identifying novel threats.
As a result, a proactive protection can be
established that adapts to changing trends in communication and
attack development.
Proactive Protection of Services
The first goal is the development of
techniques for protecting communication services, e.g. services for
Internet Telephony (VoIP) and Internet Television (IPTV). These
services use variable and changing protocols. Thus, there is a need
for methods capable of automatically learning structures of
protocols to mimic their functionality and to bait attacks ("Honey
Services"). These electronic decoys facilitate the development of a
proactive attack detection, which automatically analyzes the
collected data for identifying and stopping upcoming threats.
Proactive Protection of Devices
The second goal of the project is the development of methods
for the protection of end user devices, like IP telephones,
smartphones and mobile computers. The diversity and multitude of
these devices makes threat detection from within the devices
difficult. Hence, attacks need to be fend off before reaching the
devices. To this end, techniques from machine learning are applied
for analysis of mobile applications and communication content. In
combination with electronic decoys ("Honey Devices"), they also
contribute to the proactive protection of communication.
Adaptive Monitoring
Besides services and end user devices, the infrastructure
itself can be a target of possible attacks. The third goal is thus
the analysis and detection of global security problems within the
infrastructure. To reach this objective, robust methods for dynamic
and adaptive monitoring are developed that operate under locally
and temporally fluctuating traffic. Based on the monitored data and
observations of the electronic decoys, an automated threat analysis
and early warning can be conducted, permitting the identification
and visualization of security breaches and anomalies within the
infrastructure.
With the increasing convergence of communication to IP-based networks, dynamic and adaptive protection against security threats becomes a critical requirement. Unfortunately, convergent communication is characterized by complex network protocols, heterogeneous infrastructures and a multitude of user devices. Today's security instruments fail to cope with this diversity; communication services as well as clients regularly fall victim to network attacks and malicious software.
The project PROSEC aims at establishing a holistic protection for convergent communication. This protection builds on three layers: (a) the protection of services, (b) the protection of devices, and (c) the adaptive monitoring of the infrastructure. The following figure shows these three layers. Information about current threats are collected using dynamic decoys and analysed with machine learning for automatically identifying novel threats. As a result, a proactive protection can be established that adapts to changing trends in communication and attack development.

The first goal is the development of techniques for protecting communication services, e.g. services for Internet Telephony (VoIP) and Internet Television (IPTV). These services use variable and changing protocols. Thus, there is a need for methods capable of automatically learning structures of protocols to mimic their functionality and to bait attacks ("Honey Services"). These electronic decoys facilitate the development of a proactive attack detection, which automatically analyzes the collected data for identifying and stopping upcoming threats.
The second goal of the project is the development of methods for the protection of end user devices, like IP telephones, smartphones and mobile computers. The diversity and multitude of these devices makes threat detection from within the devices difficult. Hence, attacks need to be fend off before reaching the devices. To this end, techniques from machine learning are applied for analysis of mobile applications and communication content. In combination with electronic decoys ("Honey Devices"), they also contribute to the proactive protection of communication.
Besides services and end user devices, the infrastructure itself can be a target of possible attacks. The third goal is thus the analysis and detection of global security problems within the infrastructure. To reach this objective, robust methods for dynamic and adaptive monitoring are developed that operate under locally and temporally fluctuating traffic. Based on the monitored data and observations of the electronic decoys, an automated threat analysis and early warning can be conducted, permitting the identification and visualization of security breaches and anomalies within the infrastructure.
